Rethinking identity beyond passwords
Your password isn’t protecting you.
At least not in the way you think. Not anymore. We’ve built a whole mythology around passwords — how long they should be, how often they should change, what characters to include. We treat them like they’re the foundation of our digital security.
They’re not.
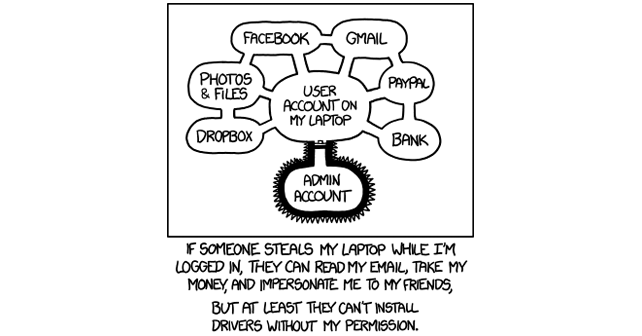 Source: https://xkcd.com/1200/
Source: https://xkcd.com/1200/
Usually, I don’t run security workshops. Most of the time, I’m there to talk about AI strategy, automation and custom apps with Power Platform and Azure, licensing and governance. But still every single time someone will eventually ask about passwords. Usually in a side comment. Should we increase password length? or Is it okay to allow password managers? or even What is a reasonable password policy? IT forces us to change passwords every 6 weeks!
It’s like a reflex. And every time it comes up, I realize just how much confusion and outdated thinking still surrounds this topic. Most of the ideas we still cling to about password security are based on assumptions that stopped being relevant many years ago. We’re still designing policies to protect against brute-force attacks — as if that’s the main threat. But in the real world, that’s the last thing an attacker tries. Before anyone even considers brute-forcing your password, they’ll try credential stuffing (using leaked passwords from another site). They’ll phish you with a fake login page. They’ll deploy malware to log your keystrokes. They’ll trick you into giving it away — and nine times out of ten, that works.
That’s the real threat landscape. And none of it is stopped by making your password a few characters longer or swapping a for @ or - as we collectively all decided, once vendors made it mandatory that at least one character needs to be a special character - adding an ! at the end of our existing password. So no, I don’t really care whether your password is 12 or 16 characters. It’s good practice to avoid reuse and common phrases, sure. But password strength is no longer a meaningful line of defense. If your identity strategy starts and ends with make better passwords, you’re solving the wrong problem.
What does work?
1. MFA
Multi-factor authentication changes everything. It stops account compromise even if the attacker has your password. And the numbers don’t lie — Microsoft’s own data shows that enabling MFA prevents over 99% of identity-based attacks. It’s not just effective; it’s essential. That’s why Microsoft enforced MFA for all accounts. But we can go further. And frankly, we should.
2. Passwordless authentication
Passwordless authentication with FIDO2 keys, Windows Hello, authenticator app push approvals, certificate-based logins: these are harder, better faster, stronger and far more secure than any password ever was. They’re phishing-resistant by design. They eliminate the weakest link: the password itself. When someone logs in with a biometric, or a device-bound key, or a hardware token, there’s nothing for an attacker to guess, steal, or reuse. Of course, going passwordless requires planning. You need a phased rollout, support for fallback methods, alignment with your Conditional Access policies. But it’s achievable — and honestly, overdue. The guidance is there. The tooling is mature. And the risk of doing nothing is growing. So the next time passwords come up — and they will — this is the conversation we need to have.
Not about complexity requirements or expiration intervals. Not about special characters or clever passphrases.
But about what actually works. What actually stops breaches. What actually reflects the modern threat landscape.
It’s time to start treating passwords as the liability we’ve failed to let go of.
You May Also Like
Confidently wrong: Why we misquote Maslow and misunderstand AI
Maslow never drew a pyramid, yet it became one of the most repeated (and misunderstood) frameworks in business. This blog explores how that misinterpretation spread—and how the same pattern is now …
Your Testing strategy is broken - Let’s fix it
Too many teams chase 100% test coverage and end up testing the wrong things. This post breaks down why coverage isn’t quality; and how to build a smarter testing strategy that protects what matters: …
Tired of the AI hype machine
LinkedIn is full of AI vision posts, chatbot demos, and elephant memes. But inside real organizations, most AI projects stall at generic chat interfaces that solve nothing. This post cuts through the …





